1. Introduction
One of the world's most revolutionary technologies has been discovered, known as the blockchain, a disruptive platform that transforms many aspects of life (Ensmenger, 2018; Skinner, 2016; Whyte, 2019). Every individual needs to focus on understanding the science of blockchain, because basically the use of blockchain technology has high potential to change various industries in various ways (Beck & Müller-Bloch, 2017; Rahardja, Bist, et al., 2020).
Blockchain is a ledger of decentralized digital transactions without control by individuals, groups or companies, so that the data structure that has been available cannot be changed (Mattila, 2016). Because if the information submitted is wrong it will cause problems. Databases can only be added without being deleted so that each transaction will be summarized into a new block that continuously forms a chain, this eternity makes the blockchain different from ordinary databases (Bergstra & Burgess, 2018; Sunarya et al., 2020).
Various industries, businesses and even governments have been captivated by the charm and sophistication of blockchain technology, with a transparent transaction database also distributed. In particular the financial industry which initially rejected blockchain technology, is now beginning to learn to understand how the system works and the impact of the blockchain (Peters & Panayi, 2016; Teece, 2010).
A thorough Bibliometric Analysis and Review of 387 blockchain research has been conducted, and the six most popular keywords were found, including 66.7% regarding Smart Contact, 11% regarding Ethereum, 8.8% regarding Distributed Ledger, 6.7% regarding Crypto-currency, 4.8% regarding Security, and 2% regarding the Supply Chain (Ante, 2020). The remaining subject interests are relatively insignificant in terms of research attention given by the world blockchain scientists. It caught us by surprise how few have given any attention to blockchain application in education. Like other economic sectors, looking at the challenging problems facing the education sectors, blockchain technology presents the most potential to solve current issues and leapfrog to a new way how education could be conducted like never before. We are all aware that this can only happen if many scientists collaborate on innovation and scientific discoveries on using blockchain technology in the education sector. Mexico already launched blockchain pilot programs for Mexican specific elementary schools (Franzoni et al., 2019). This research aims to achieve similar or better results for Indonesian specific implementation in tertiary education.
The focus is on greater attention to building blockchain applications to enhance learning objectives and increase competency attainments and personal information securities in the educational sectors (Alammary et al., 2019).
Therefore, the world of education also does not want to be left behind by today's sophisticated technology, where blockchain can be adopted by educational institutions, especially in profiling each individual with the final result in the form of a certificate in digital form equipped with blockchain sophistication (Rahardja et al., 2019). This is necessary because of the prevalence of falsification of diploma data in educational institutions in Indonesia, so the quality of Human Resources (HR) is questionable. This study confirms that information distribution activities can be controlled and personalized properly using blockchain-based digital certificates which have a significant effect on public satisfaction and data security (Hariguna et al., 2019; Rahardja & Raharja, 2009).
The novel contribution mainly emphasizes exploiting blockchain technology in the education sector within Indonesia. There are still many internet connectivity problems in rural areas and towns through Indonesia's educational institutions' geographic distribution. Even though they have implemented a server system in the ministry in urban areas, they still rely on local servers in their respective institutions. The existing data management still applies to a single server database. And according to the Three Tier Architecture or better known as the Client-Server Programming concept, it requires the availability of a User Interface that can facilitate clients, flexibility in access to servers and databases because the work is carried out separately without any influence from other layers. If additional features can be done coordinatively in each existing layer, this can be beneficial in creating and developing a secure application. In that case, the data is more resistant to security hacks so that the authentication of every processed information is guaranteed, and usability utilization becomes robust.
Figure 1. A study was made in which the results of profiling to be included in the certificate need to be encrypted so that it has 2 keys to be able to open it, namely public key and private key (Komputer, 2013; Muzayana et al., n.d.). Then the key needs to be applied also hashing so that the certificate cannot be falsified by irresponsible parties (Heriyanto, 2016). Blockchain in a certificate can be used to determine the validity of data (Yusup et al., 2018). As well as reducing the burden of monitoring an admin to maintain the stability of data security that is vulnerable to problems (Nurhaeni et al., 2019).
2. Research Methods
Qualitative research methods were adopted in this study, there are three approaches such as literature review, case studies, and library research to produce research evidence (Guritno & Rahardja, 2011). With the advent of blockchain technology, the qualitative method presents a pragmatic approach in involving current technology in the initial stages.
Despite the rapid development of cloud computing technology, security and trust in data is still a major challenge (Wei et al., 2020). Problems that are present in the future will be increasingly challenging for higher education. Especially regarding the validation of documents that require a new revolutionary tool (Lizcano et al., 2020). Apart from the increasing interest in blockchain, which is still classified as a new topic, research is being conducted to introduce better blockchain, especially in the field of education (George et al., 2019). Over time the evolution of research has resulted in major discoveries and has been done through detailed analysis (Dabbagh et al., 2019). Where has been carried out a survey of smart communities who independently use a revolutionary technology as a key component (Aggarwal et al., 2019).
The level of information security and data transparency can be improved through a technology called blockchain, because it is ensured to have high integrity in achieving the confidentiality of records or data (Lee, 2019; Pal et al., 2019). Immutable code can be used to prevent undetected updates from data or information that has been stored in an agency database (Liu et al., 2017). Then the encoding rules for mapping information sequences using immutable code also need to be applied (Aini et al., 2020).
In addition to using immutable code, seeking ubiquitous technology can make security more complex and more difficult to solve (Sellami et al., 2019). In the problems that arise at this time, educational institutions are so rampant, open and ubiquitous, so that professionals at the company need time to be able to validate every prospective new employee (Lizcano et al., 2020). To make transactions or transfer data securely, authentication is the main thing in order to help the network reduce illegal users and prevent fraud. Because the data authentication process effectively identifies users well. So that the authentication process that will be performed can prevent security attacks on user data (Rahardja, Hardini, et al., 2020).
Quoted from WoS from 2013 to 2018, studies show that researchers have changed their research interests from Bitcoin to Blockchain in the past two years. There are four fields of research, namely Computer Science, Engineering, Telecommunications and Business Economics, where most papers or research scientific papers cover Blockchain technology (Mohammed et al., 2020). Blockchain keeps a permanent record and transaction history, but nothing is truly permanent. Immutable blockchain records are based on immutable networks. In the context of the blockchain, it means that most members of the blockchain community must agree to change information and incentives not to change data (Laurence, 2019).
Through blockchain technology, facilitates the development of equipment and great trust, where an authorized party needs to ensure the quality of secret codes as a method of data security (Zeng et al., 2019). Although the main role of decentralized ledgers, such as blockchain, is storing data related to interactions between users to build trust, that is not enough, because blockchain technology has the possibility to offer better functionality and sophisticated quality (Hu et al., 2018).
Nowadays mesh networking and blockchain are the two hottest technologies in the telecommunications industry. Combining the two technologies can produce a new formula again regarding internet access. Mesh networking makes connecting to the internet easier and more affordable, when the blockchain merges in mesh networking technology, making internet access increasingly high selling points by enabling sharing of bandwidth for crypto-tokens (Selimi et al., 2018). Besides the blockchain technology is also proposed as a coordinating tool to support the non-monotonic consistency requirements of the IPFS system, because IPFS presents a peer-to-peer system that allows data distribution through the internet network (Tenorio-Fornés et al., 2018). Where all the popular companies engaged in blockchain technology use the Elliptic Curve Digital Signature Algorithm (ECDSA) (Durand et al., 2018), and so the hidden novelty and benefits of blockchain technology can serve as a tool for designing smart cities and social structures. The greater use of blockchain technology, the possibility to have a new mode of social organization will also increase (Swan, 2018).
Blockchain technology also has the potential to be able to contribute in various fields, where the application of blockchain technology in the energy and industrial sectors has been successfully carried out, but there has been no application in the education sector specifically in the certification section (Brilliantova & Thurner, 2019; Hughes et al., 2019). If certificates in the world of education can be embedded with blockchain technology optimally, then educational institutions can improve the quality of data security and the level of originality of the data held.
But the use of blockchain technology to track physical assets is not new. Technology that can track products used to be based on an RFID chip, one limitation is scalability with regard to the number of transactions that can be processed by the network. This can be overcome by protecting and monitoring using unique patterns. Using a hash that can ensure data privacy, timestamp is also a consideration as evidence of the existence of immutable data, with this approach, the integrity of data tracking cannot be contested (Hepp et al., 2018).
So, it can be concluded through previous research, that knowing the features of blockchain technology in depth can have an effort to show how the blockchain can be programmed and implemented for many people is not limited to cryptocurrency (Singhal et al., 2018). Because in practice in the world of education the community also takes part in requiring a high level of security to be able to maintain privacy and the level of originality of a certification.
2.1. The Accuracy of The One-User Verification Process
With the validation stage using public keys and predefined parameters to calculate the verification equation, it can be concluded that the integrity of the data is damaged. In the case of complete data, the parameters do not change, and the left and right sides of the verification equation are calculated respectively.
Equation from the left side:
Equation from the right side:
Proof:
It can be seen that the equation is the same on both sides. Since parameters a and b are both publicly available, only if the parameters in the formula are changed, there will be an imbalance between the two ends of the equation, and cloud server-side data can be changed. Therefore, by determining the balance of the equation, it is determined whether the data integrity is still intact.
3. Results and Discussion
Blockchain employs some smart incentives to maintain honest agencies, this is to ensure the stability of the network now and in the future.
Blockchain-based certificate units are based on proof of work, which requires the expenditure of time and energy by each agency that must obtain, manage and operate a blockchain-based digital certificate engine.
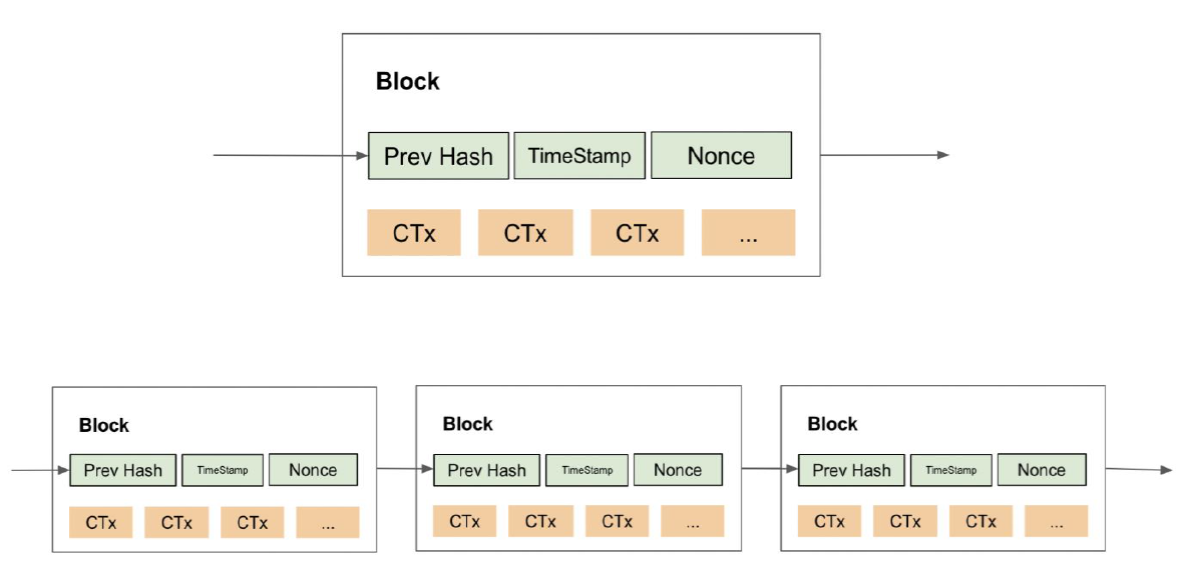
Figure 2. Where each certificate transaction (CTx) will be tested whether it is considered valid. Transaction is valid if it follows the rules and according to the structure, if multiple transactions are considered invalid. In addition to conveying these valid transactions, some nodes also provide computing power to the network by putting all valid transactions they receive into blocks. Where each block arranged linearly is called blockchain. The hash-based structure is one of the most promising candidates to be used in this study because it can help certificate data security (Ma et al., 2020). Operational patterns and file behavior can be monitored based on timestamps so that they can be recorded in the ledger for each block transaction that is carried out (Ho et al., 2018). Nonce itself is a method of generating random values that can be used for authentication, most nonce-based authentication schemes require verification tables that are stored on the server to store nonce in the next authentication session (Zainuddin et al., 2017).
Based on the current decentralized file system observation capacity as a metadata statement about the existence of digital resources that cannot be changed in this study is called immutable. The Interplanetary File System (IPFS) as a basic example of supporting infrastructure with minimal convention sets, can be used as an alternative mechanism for storing byte streams in digital repositories such as DSpace or CKAN (Sicilia et al., 2019).
Ubiquitous technology is a contemporary innovation that significantly revolutionizes the way agencies are connected and interact with various stakeholder interests. Agencies can obtain user opinions regarding blockchain certificate services and can collect data about user behavior and habits. On the user side itself can have the advantage of accessing blockchain-based certificates anywhere, anytime without constrained access via mobile phones that are easy to carry anywhere (Margulis et al., 2020).
3.1. Asymmetric Transmission
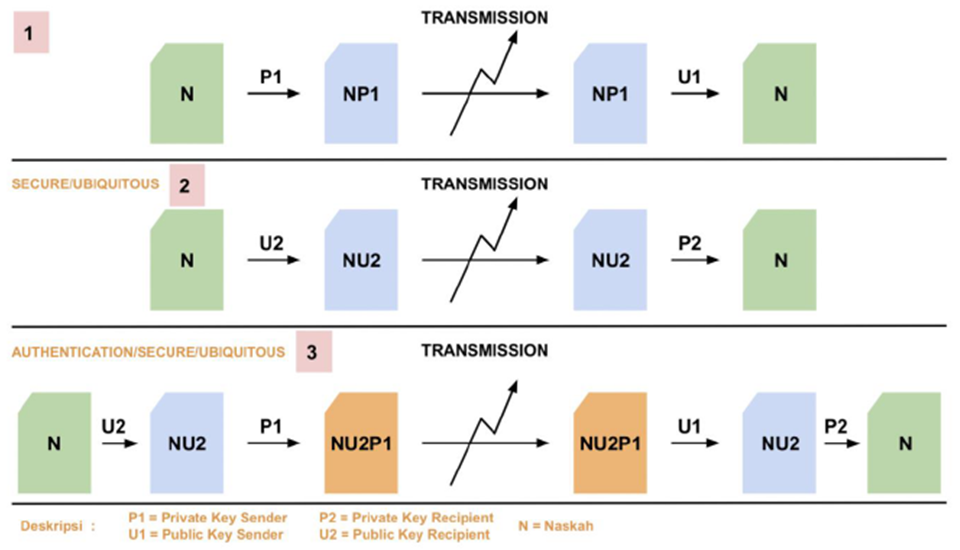
Something that is encrypted using a public key cannot be decrypted with the same public key or any key in the world, except with its private key pair. And something that is encrypted using a private key cannot be decrypted with the same private key or any key in the world, except with its public key pair.
Figure 3. Describes how Asymmetric Transmission works, there are 3 (three) key application methods with the best level of security located in the third method.
Because if we examine deeper in the first method, there are only a pair of keys to perform a data transaction. Allow illegal users to still be able to open scripts using the public key sender, which is published on the internet.
Another case with the second method, where the script is locked using the recipient's public key so that after the data is sent properly, the recipient's private key can only be opened. But this second method also has its own problems, where if there are illegal users who also listen to the plan between the sender and the recipient, then the illegal user can still send texts containing different information. This explanation makes the second method safe, as well as ubiquitous, but the information received has not been authenticated and good.
Then a third method is made, where each user has a pair of keys called P: Private Key, and U: Public Key. It was explained that if you want to do a script, document or data transaction with other users, it requires a double level of security.
The first step of the sender is to lock a script that you want to send using the Public Key recipient that is obtained through the internet, then do security again using the Private Key owned by the sender. After the manuscript is sent, the way to open the manuscript is to use a Public Key sender that is retrieved via the internet, then reopened using a Private Key that is only owned by the recipient.
With the double security level as described above, each data transaction process will be assessed as Authenticated, Secure as well as Ubiquitous. So, the script can be sent to other users without worrying that other people who are not responsible can find out the contents.
3.2. Linear Coding System
| <h2 id="1">SHA256 Encoder</h2>
<form id="hash_calculator" method="post"> <label class="nostar" id="label_hash_calculator_source_text" for="hash_calculator_source_text"><input type="radio" id="hash_calculator_source_text" name="source" value="text" checked> From a character string</label><br/> <label for="hash_calculator_plaintext">SHA256 plain text or password</label><br/><textarea name="plaintext" id="hash_calculator_plaintext" class="mini">dCode</textarea><br/> <label class="nostar" id="label_hash_calculator_source_file" for="hash_calculator_source_file"><input type="radio" id="hash_calculator_source_file" name="source" value="file" > From a file</ label><br/> <label for="hash_calculator_file">File</label> <input type="file" id="hash_calculator_file" name="file" style="margin-left:1em;" /> <span id="hash_calculator_file_span"><span id="hash_calculator_file_text"> </span> <a href="javascript:;" id="hash_calculator_file_remove">[X]</a> </span> <input type="hidden" id="hash_calculator_file_file" name="file_file" value="" autocomplete="off" /><br/> <button post="source,plaintext,file">Encrypt </button> </form> <!-- advert --> |
Explain how the process of changing encrypted data into 64-digit SHA-256 hash codes.
6KXeBs2QN9W46R2eZt4huMDsDlGRKxSJ2nfQEaR_SOE=
3.3. Research Result
Blockchain systems often use 'one-way' mathematical functions that map variable size data and vary into a fixed size data that is often referred to as a 'hash function'.
This study uses the SHA-256 hash function, where SHA-256 (256 bits) is part of the SHA-2 cryptographic hash function, designed by the US National Security Agency (NSA) and published in 2001 by NIST as the Federal Information Processing Standard AS (FIPS) (Adiyanto & Febrianto, 2020).
The SHA-256 Encryption Method has more substance compared to MD5, because basically MD5 is still vulnerable in dealing with collision attacks. Where in August 2004 at the annual cryptographic conference in Santa Barbara, California, a group of cryptographers succeeded in making two files with different content that have the same MD5 hash so that it is proof that MD5 can still occur a 50% probability of collision for MD5 there are still 2^64 or 1,8x10^19 (Sudaryono et al., 2019).
A SHA-256 processor specifically, performs 64 iterations, more than 512-bit message blocks and 256-bit hash values are described as 32-bit, where hash messages consist of 256-bit lengths and contain a 64-hexadecimal digit code (Aini et al., 2019). For that data security system which is considered to have optimal substance is recommended to use the SHA-256 hash (Guustaaf et al., 2020; Maulani et al., 2020).
Figure 4. Explain that the blockchain-based digital certificate needs to be embedded with a QR Code whose source is the processed code or a private key. This is needed for a more optimal level of network or data security.
Figure 5. Where each profile data that has been converted into a certificate is then made into a hash code, a QR Code and a digital signature on a certificate are also embedded. Then generated a digital certificate based on the blockchain protocol.
However, something like a certificate that is given a QR Code and used as a hash, and even then, cannot be a picture of a blockchain protocol that works well, because basically if a hash has been embedded into a certificate, then the certificate is used as a hash again, then will produce a different combination of hash codes.
So, this research produced another method to keep embedded blockchain technology in the certificate. Where a certificate that has been created, needs to be check certificate from a hash.
Figure 6. An official website posting to the Alphabet Incubator Blockchain (ABC) is a hash code derived from the certificate used as a double security technique.
The final result of data transformation is described as a digital certificate authenticated using the blockchain protocol. The hash code and QR Code are embedded on the digital certificate for convenient access via the official website.
In accordance with the results of the research that has been described, then to reduce the level of forgery of certification of an institution, especially education, blockchain technology as a hexadecimal 64-digit hash code and data security in the form of a QR Code can be implemented. As well as digital certificates generated in research can be said to have immutable, ubiquitous and authenticated values.
3.4. Validation Process
Each certificate that has been embedded in the blockchain is validated in the Verify menu section.
Figure 7. Users have options to upload files in PDF format. The results will be displayed with complete information about the blockchain authentication.
Figure 8. shows the Blockchain Field section that this certificate has been authenticated, with a document hash included. There are two types of document hashes made in this implementation: a unique hash from ABC with the letter ABC code at the beginning of the hash and a unique hash from Vexanium. Vexanium is a public blockchain that works asynchronously to link each certificate to the blockchain.
Figure 9. displays certificates linking the blockchain system. Due to its transparent property, every certificate embedded with a blockchain hash can be authenticated on the ABC official site and subsequently auto verified on the public blockchain https://explorer.vexanium.com/ by comparing the corresponding Vexanium hash listed in details certificate information.
This implementation can be considered unprecedented novel in the development of blockchain technology. There has not been sufficient research discussion on the authentication and validation of certificates to the extent of our knowledge. Many blockchain types of research focus more on cryptocurrency (Alammary et al., 2019; Franzoni et al., 2019). Thorough dissemination of authenticating certificates embedded in blockchain in the form of digital assets has been layout comprehensively.
4. Conclusions
Based on the results and discussion that have been outlined, it can get 7 (seven) conclusions in this study, namely:
1. Data security built into the blockchain protocol are some of the most important innovations in the history of computer science and data security education.
2. An education certificate collaborated with blockchain technology ensures data has immutable character.
3. The blockchain technology used in securing educational institution certificate data in this study is SHA-256.
4. Blockchain-based certificates that are created in digital form allow it to be stored for a long period of time.
5. Blockchain can serve various purposes and focus on various aspects, such as security, speed and versatility.
6. Blockchain technology has the potential, not only to align with the development of smart cities, IoT, and circular economy, but in relation to the internet, to form a base layer to enable these technologies to reach their full potential.
7. Six universities have currently participated in a joint consortium to implement this blockchain protocol to digital assets. More universities in other parts of the countries, particularly in remote areas, have agreed to join the consortium soon. If this happens, we can convince more stakeholders to participate in the platform and create a more grand scale holistic scheme of blockchain networks securing digital assets in educational institutions.











 nueva página del texto (beta)
nueva página del texto (beta)